The blockchain community has seen a huge influx of new members over the last months of massive economic growth. Unfortunately, many of the newcomers are not well-informed investors, but rather inexperienced speculators following a trend, with no idea what the whole fuzz is really about. As blockchain investments are a risky proposition during this early phase of adoption, I will try to shed some light on the fundamentals of blockchain technology in the hopes that it will help some people to make more informed decisions.
Sending Trusted Messages on the Internet
In order to understand the practical usefulness of blockchain technology, we need to take a quick look at the history of cryptography. The original approach of exchanging confidential messages between two parties was to encrypt it with a key on the sender’s side, transmit it and decrypt it with the same key on the recipient’s side. This concept is called symmetric cryptography and works well when you can securely exchange the key.
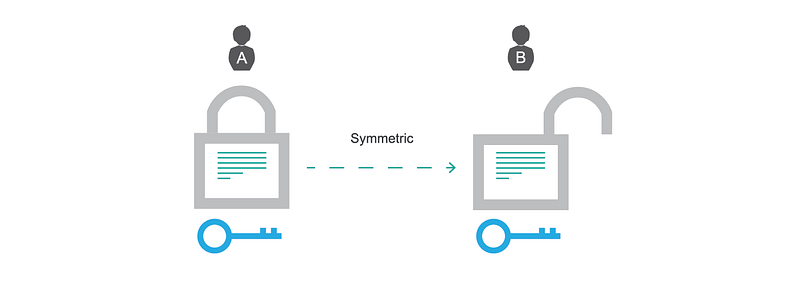
Symmetric encryption uses the same shared key on both sides.
With the spread of the Internet, it has become less practical. How do you securely exchange the key when you do not have a trusted channel? It wasn’t until the arrival of asymmetric cryptography, which can be traced to the early 70s, that encryption became both feasible and practical on the Internet. In contrast to the previous method, asymmetric encryption uses two keys: a private key and a public key. Anyone will be able to encrypt a message using the public key, but only the private key will allow you to decrypt the message.
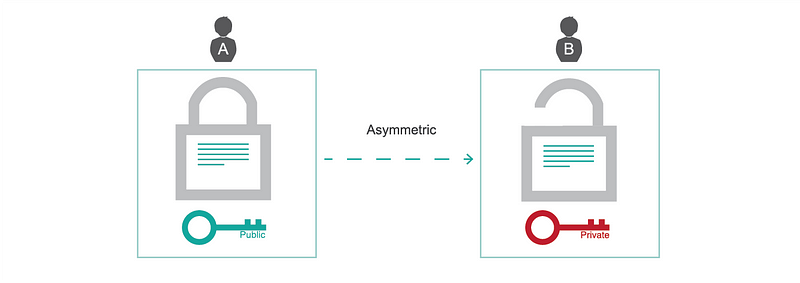
Asymmetric encryption uses the public key for encryption and the private key for decryption.
In reverse, it is also possible to encrypt something using the private key. In that case, anyone holding the public key will be able to decrypt it and read the plain text. By asking a person holding the private key to encrypt a specific text, we can verify whether he really has access to the private key, without revealing it. This process is used to sign messages and allows us to authenticate the origin of messages on the Internet. Combining the first concept (encryption) with the second concept (cryptographic signatures), we can exchange confidential messages with an authenticated origin.
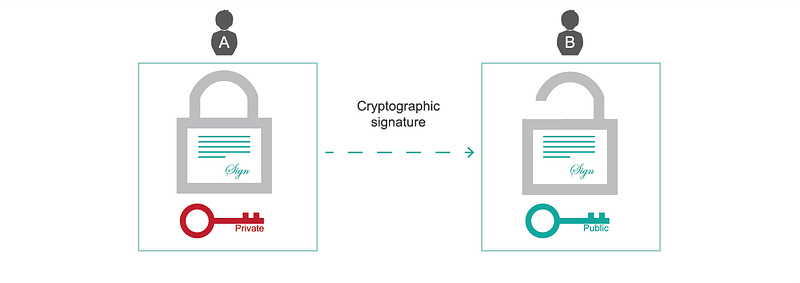
Digital signatures use the private key to encrypt specific data, which can then be verified with the public key.
If we apply this to the transfer of value on the Internet, you can create and sign a message saying “Bob sends Alice a hundred dollars.” This could lead you to believe that it is easy to create a system to exchange value. If you look at it in detail, however, a number of fundamental problems stand in the way of secure online transfers of value. In fact, these obstacles are so hard to overcome that no one managed to build a working system before Bitcoin.
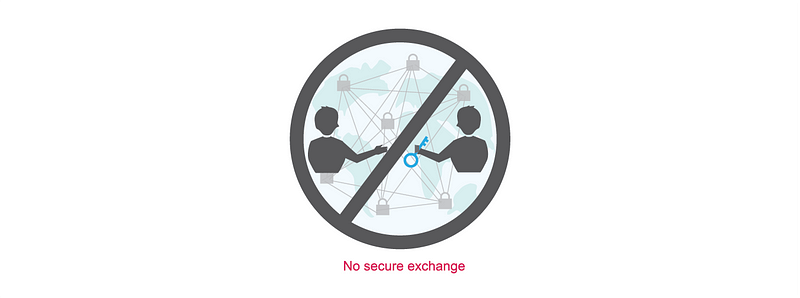
With symmetric encryption, we lack the secure exchange of shared keys on the Internet.
The Double Spend Problem
Imagine you want to transmit some value to your girlfriend. Let’s use an imaginary unit of account and let’s call it it Bitcoin (because, you know, coins are money and Internet stuff is all bits and bytes). In a first step, we will use asymmetric cryptography and consider that everyone has a key pair. The public key corresponds to your account number and holds your balance, while the private key allows you to sign transfers from your public key to someone else’s public key.
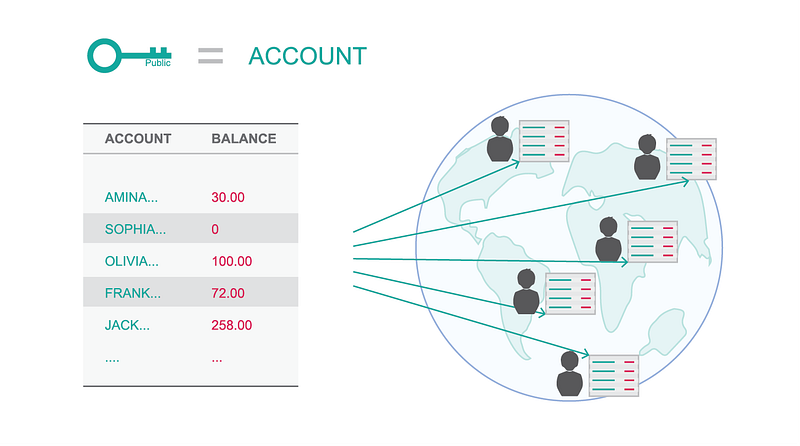
The public key corresponds to the account with its corresponding balance.
In that scenario, you can indeed create a message that reads “I transmit one bitcoin to Sophia” and sign it with your private key. Everyone can keep track of all balances by keeping a list of accounts and updating it when receiving valid messages. They can check the signature of the message and look up the available balance of your public key. With this naive approach, we have a rudimentary digital money system. As we will soon see, this configuration is vulnerable and people would be able to exploit it.
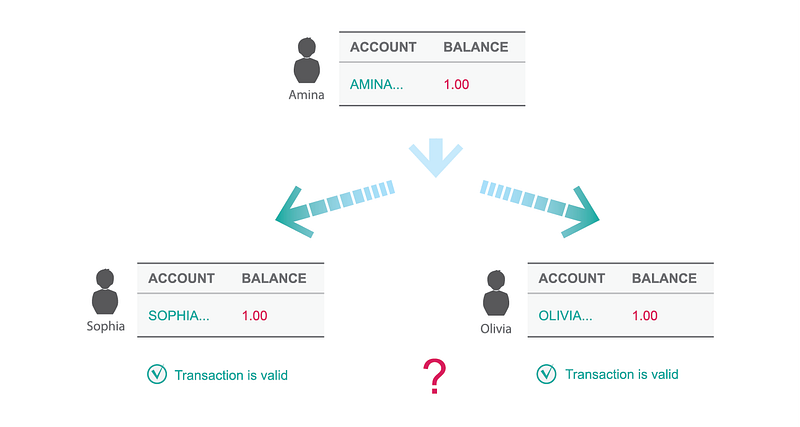
Two transactions which are cryptographically valid will conflict if they try to spend the same balance.
The double spend problem describes an event where someone tries to send the same one bitcoin balance to two of his girlfriends. Suddenly, both Victoria and Olivia think they now own the one bitcoin. There is a conflict between their respective public key balances. The problem is that there is no way to decide which one of the two transfers is valid; everyone wants their bitcoin, so they insist on their view of the balances. In a simple system of agents operating in their own self-interest, there is no way to resolve this conflict.
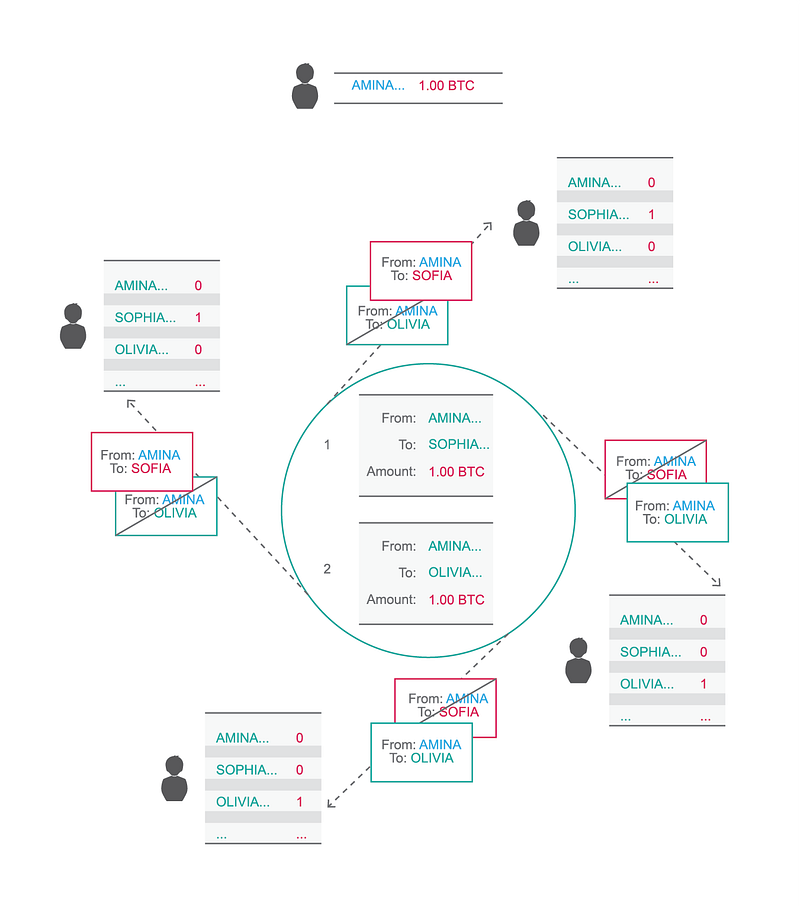
The conflicting transactions will create a mismatch of the ledger on the network.
The Byzantine Generals’ Problem
A second issue we run into is related to consensus in systems where we have no way of trusting the participants of the network. To simplify the original description of the problem, picture five generals who have surrounded a city. They want to decide on a common strategy: attack or retreat. If the majority joins, an assault will be successful. If all generals act in good faith and the means of communications are reliable, they can coordinate and proceed.
As long as the majority of generals agree, you could assume that nothing can go wrong. This assumption is wrong, however, if we introduce the existence of potential malicious actors. The honest generals are no longer able to trust the messages of their peers, while the conspiring parties know exactly what is authentic information. In this way, bad actors gain an informational advantage. For instance, a single malicious general can doom two generals to defeat by telling them he will join their attack and simply not doing so.
In a general way, the problem can be described as the impossibility to agree on a common decision in a network with possible malicious agents or unreliable messaging, even if the majority of participants is honest. In terms of the system of accounts described earlier, for instance, one angry ex-girlfriend could lay waste to the validity of all balances, even if all other participants are exchanging value in a good faith.
To make matters worse, this problem has been proven to be unsolvable in theory. In practice, society chose a simple workaround: two parties which want to initialize a transfer of value agree on a trusted third party. The third party certifies the identity of both parties and the transaction between them. This creates a centralization pressure and leads to the formation of big hubs of trust which act as gatekeepers of the account balances.
The Overhead of Centralization
The introduction of a central authority introduces some disadvantages. Relying on central authorities for trust leads to a system with single points of failure. A breach of trust or security can lead to the loss of confidentiality, integrity or availability of balances and transactions. Inevitably, as long as someone is in charge of the definitive version of account balances, there will be human failure, fraud and abuse.
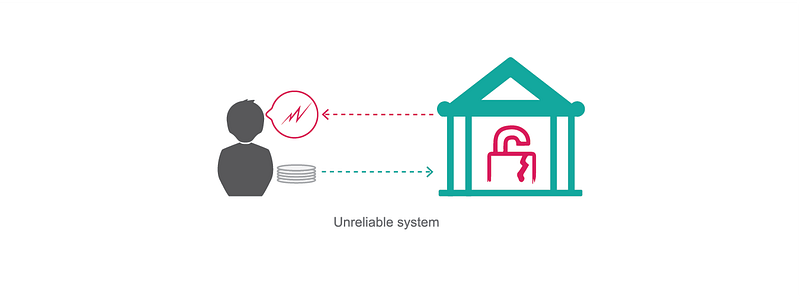
In a centralized system, a compromised third party or unreliable communication channels can cause loss of value.
In order to counteract these natural tendencies, you have to dedicate tremendous resources. The rules of governance for trust institutions need to be clearly defined and processes for the correct supervision of all systems have to be introduced. More sophisticated bad actors will lead to an increased need for control. In the end, the evolution of such a centralized system culminates in what is the modern banking system with its rules, laws and regulations.
This legacy system is riddled with inefficiencies and thus ripe for disruption. Bitcoin is so innovative because it suddenly showed up with a solution to the two fundamental problems described earlier. As an open system with a radically efficient way to guarantee trust, it made the world of value transfers accessible to anyone on the Internet. At its core, it did so by cleverly combining concepts from networking, cryptography, economy and — I would argue — psychology.
The Cleverness of Bitcoin
If you want to use the Internet to transfer value between users, you first need to establish a common language between the participants. Bitcoin does this by creating a peer-to-peer network where the participants agree on a common communication protocol. Due to its distributed nature, it is resilient to attacks and failures. This open network creates the shared foundation for a global platform of value exchange.
In a second step, cryptographic signatures are used to guarantee the integrity and authenticity of transactions. As described earlier, public keys function as the accounts which hold Bitcoin balances. If you want to transfer value to another user, you use your private key to sign the transaction and to move the funds from your public key to the public key your counterparty. We keep track of the balances in a shared ledger.
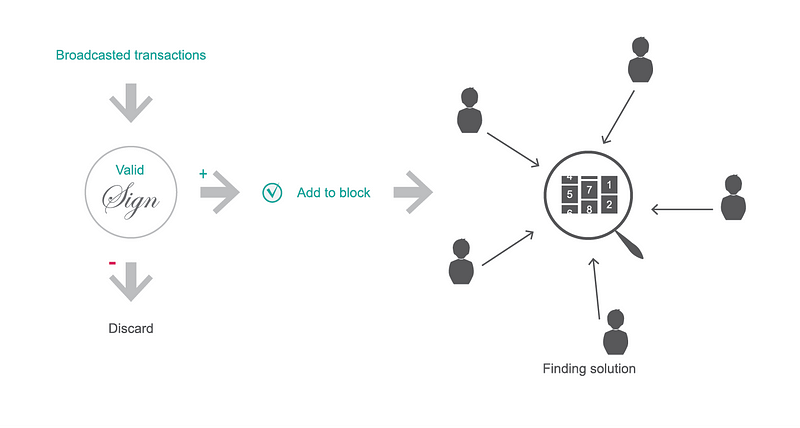
Cryptographically valid transactions are assembled into a block of non-conflicting transactions.
To make sure that we agree on the state of the ledger, Bitcoin introduces rules to resolve conflicts between transactions. The network has an algorithm to collect a new set of valid transactions at regular intervals. This block of transactions represents the transition from the current state of the ledger to the next state. It is only accepted by the network participants after a sufficient amount of computing work has gone into the assembly. By following the same rules during its creation, the whole network finds agreement and the shared ledger stays synchronized. The series of these blocks is called the blockchain.
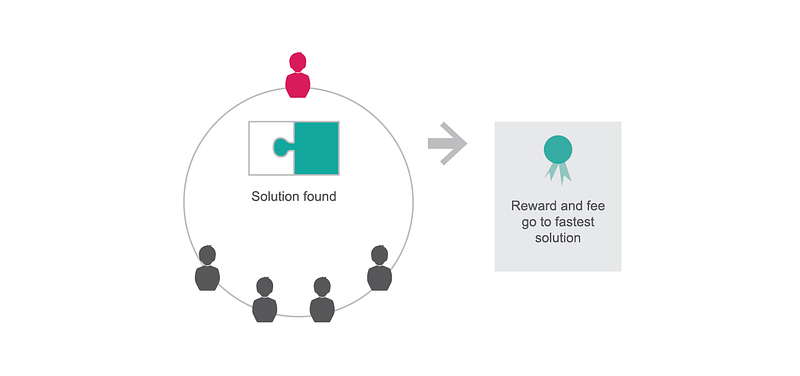
Once someone solves the cryptographic puzzle for a block, he receives a reward and the transaction fees.
Last but not least, we want to make sure that the network is robust against bad actors. We can do this by economically punishing participants who do not follow the rules of the network, while we reward those who contribute to the enforcement of the ruleset. Someone trying to attack the network for malicious purposes will have a hard time causing damage; the assumption is that normal participants work for their economic benefit and thus align on the rules which punish the disruptor.
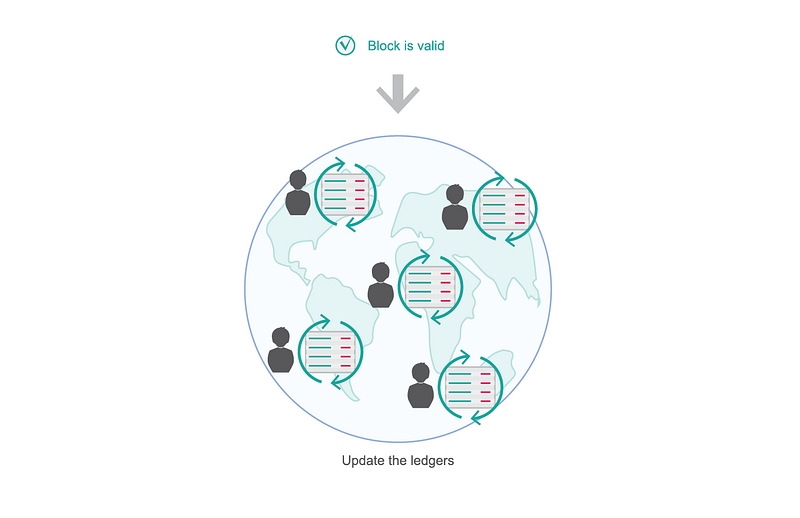
A validated block is broadcasted on the network and peers update their copy of the shared ledger.
It should be pointed out that these economic incentives are not based on mathematics, nor on economic principles alone. In fact, they rely on human nature and the assumption that we will act in our own self-interest as long we don’t have ulterior motives. This expectation holds up surprisingly well in practice and enables Bitcoin to overcome a theoretically unsolvable problem. In general, every public blockchain depends on basic human instincts to secure the network.
Moving beyond Bitcoin
When you put it all together, you have a system to find consensus on a shared state of account balances. It allows you to collectively transition from one valid version of the ledger to the next. The resulting network allows us to transfer value on the Internet without relying on a trusted third party. However, if you take a closer look, you will discover that we have a lot more than that.
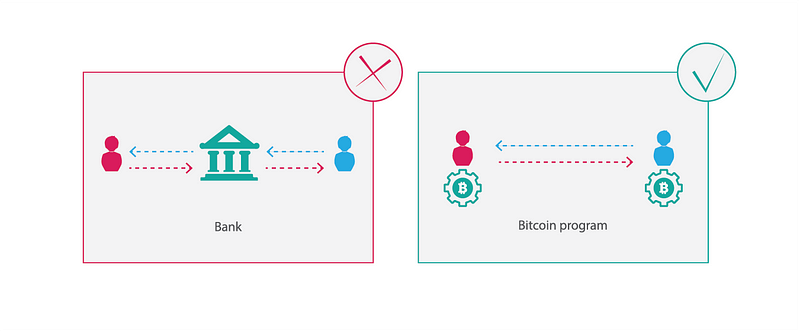
Bitcoin allows two parties to execute trusted transactions without going through a third party.
Once you consider the system in detail and start thinking a bit outside of the box, you will get to the point of asking yourself: “why can’t we just include other kinds of data into the blocks?” And suddenly, you find yourself on a journey down the rabbit hole. You will quickly come to realize the enormous implications of this line of thought and the tremendous promise that blockchain technology holds.
It was probably that simple question which lead to the paradigm shift behind all modern applications of blockchain technology. Indeed, you can imagine adding custom data to the blocks, unrelated to account balances. As long as you define the necessary rules and all participants of the network agree on its validity, the technology allows you to agree on a common state for any kind of data at all. This is where the principles of blockchain technology become truly powerful.
Picture: Creative Commons Micosiervos
This piece solely expresses the opinion of the author and not necessarily the organization as a whole. Students For Liberty is committed to facilitating a broad dialogue for liberty, representing a variety of opinions. If you’re a student interested in presenting your perspective on this blog, you can submit your own piece to [email protected].